Measures of Risk Identification and Management
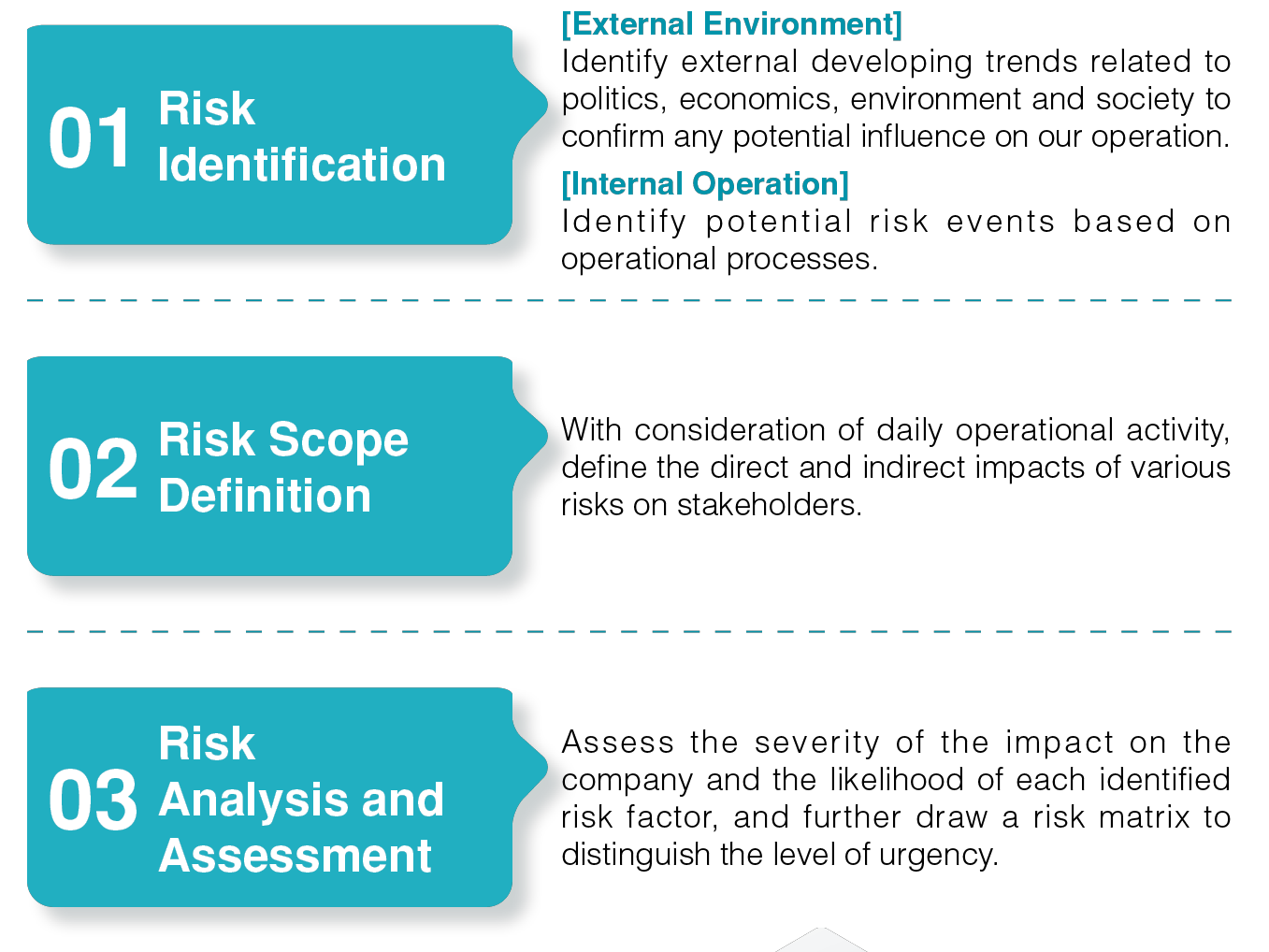
Sound risk management is the basis of corporate sustainable development. The concept of a Business Continuity Plan (BCP) was introduced by GIGABYTE. Threats, vulnerabilities, and risks in business operations are identified and assessed in order to protect operations from disaster and accidental damage. If an incident does occur then the resulting impact and interruption are minimized as well. 11 areas of risk were identified through the risk management process in 2024. Senior executives above the manager level then participated in evaluating the degree of impact on the Company from each risk and their likelihood. A risk matrix was then drawn up based on the results. The appropriate departments were then commissioned to develop a sound risk management method using their professional knowledge and practical experience in related fields.
To further strengthen the companyʼs risk management policies, GIGABYTE reorganized its Audit Committee into the “Audit and Risk Management Committee” in 2025 and launched related risk management initiatives.
Risk Management and Control Process
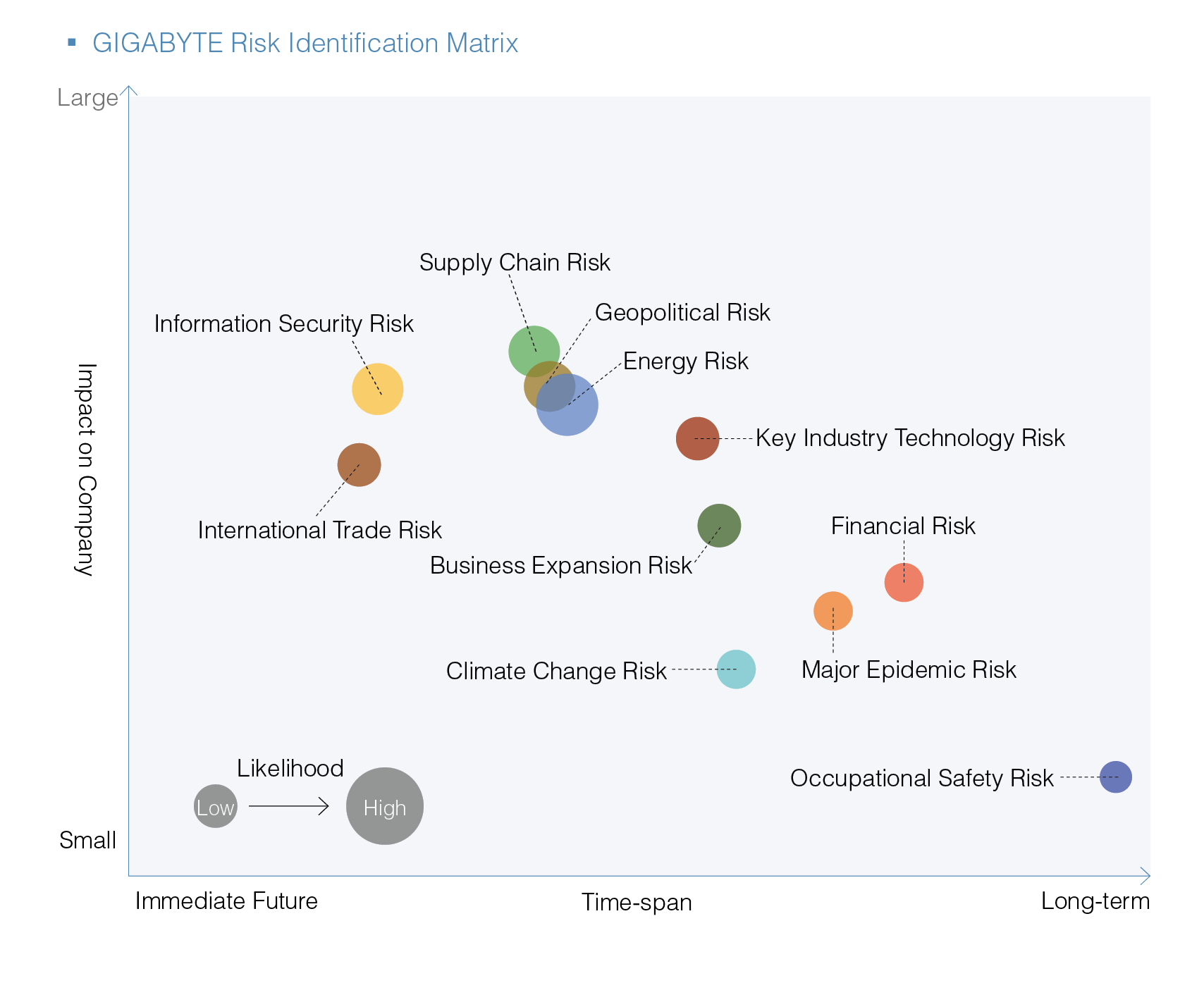
Short- to mid-term risks: 1 to 5 years
Long-term risks: >5 years
Emerging Risks
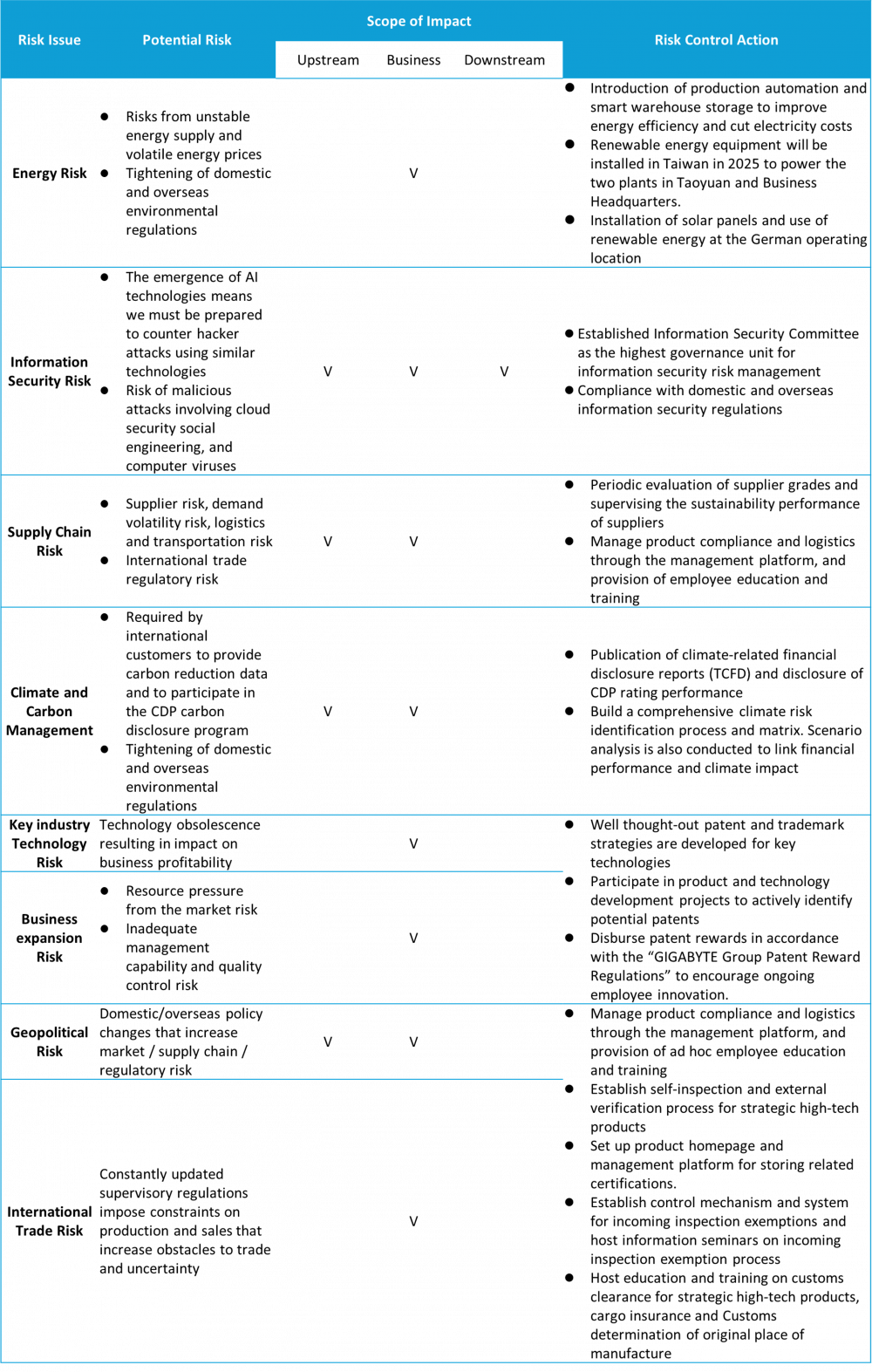
GIGABYTE periodically conducts in-depth assessments of emerging risks, such as information security, supply chain risks, and designated contagious diseases. The potential threats and impacts of emerging risks on the Companyʼs development in the future are also discussed.
| Emerging Risk | Management Action |
|---|---|
| Information security event risk | Risk management is achieved through periodic review of domestic and overseas information security regulations as well as raising employee awareness through drills. |
| Supply chain procurement and logistics risk | Suppliers are required to cooperate with a long-term supply policy with rolling demand forecasts. Green logistics has also been implemented through optimization of transportation plans, distributed logistics networks, and hybrid transportation programs. A hub warehouse model is also used to protect against political uncertainty, inflation, labor shortages, and low inventory in order to maintain the flexibility and resilience of the supply chain. |
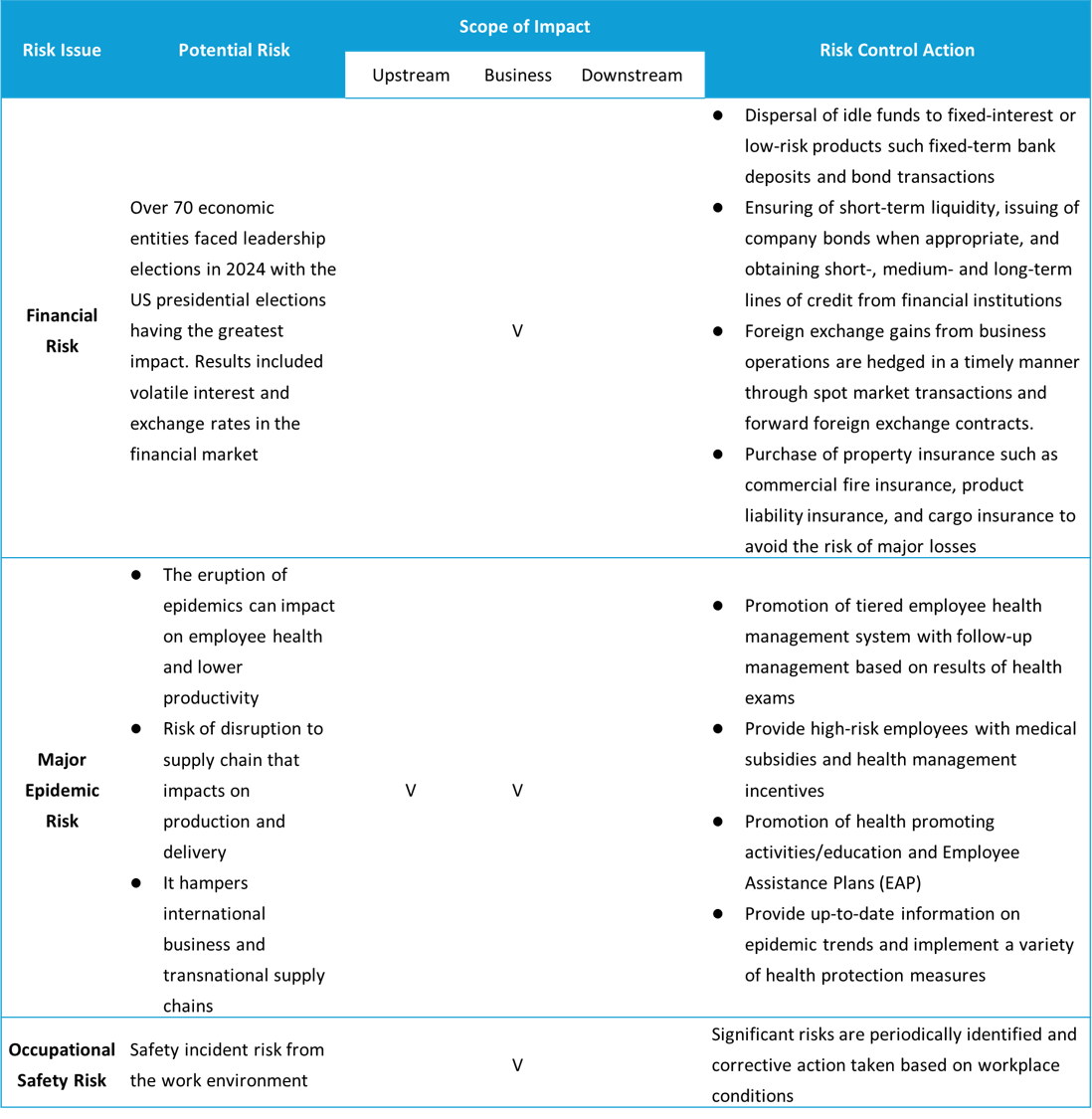
| Designated contagious disease risk | Establish reporting and emergency response mechanisms along with routine internal e-mails, posters, and host health-related seminars to equip employees for self-health management and response. |
| Green inflation risk | GIGABYTE has developed and applied green technologies, implemented the Sustainability Fund, and plans to consume renewable energy to address the rising compliance costs of domestic and international environmental policies. Meanwhile, we actively engage suppliers in carbon reduction strategies, offering energy-saving and health inspection counseling, to empower them to realize a low-carbon transition. As GIGABYTE’s upstream scope 3 greenhouse gas emissions are reduced, so will the potential carbon costs of our products. |
| Export risks associated with geo-conflict | The target markets may control cross-border transactions of specific sensitive goods, software, or technologies due to geopolitical conflicts. In response, GIGABYTE has internally used SOA to establish a shipment release mechanism, dual-use item warnings within the shipment system, invoice warnings, and export license requests. An effective proactive control program could reduce the risks of export transportation and reputational damage. |
Enhancement of Risk Culture
GIGABYTE attaches great importance to the cultivation of internal corporate risk awareness. We strive to make risk awareness a part of every GIGABYTE employeeʼs work DNA. Risk management training is implemented for all personnel from mid/upper managers to junior employees. For example, emergency incident response drills and first-aid courses are conducted every year. GIGABYTE organizes emergency no-notice evacuation drills every December. Simulated scenarios are used to implement the evacuation of all personnel (including visitors and contractors) and conduct exercises on emergency response and deployment of fire hoses by the firefighting team.
- Home
- Innovation Management
- The Guanxi Blue Zone
- The Ocean is Our Home
- From the Chairman
- Commitment to CSR
- Stakeholder Engagement
- Material Topics
- SDGs
- Corporate Organization
- Code of Conduct
- Information Security & Privacy
- Risk Management
- Supply Chain Management
- Tetralogy of Supply Chain Engagement
- Conflict Mineral
- Environmental Management Policy
- Brand Strategy and Business Reputation Management
- Climate Strategy and Risk Management
- Customer Relations Management
- Eco-friendly Product
- Extended Product Responsibility
- Biodiversity
- Circular Economy
- Green Action
- Sustainability/Environmental Education
- Green Activities
- Working Holiday
- Corporate Volunteering
- Go Green Taiwan
- Make Earth Green Again
- Tree Map
- Overview/Core Concept
- Rooftop Farm
- Ecology Photo Competition
- Resource Hub
- Diverse and Inclusive Workplace
- Talent Management
- Human Rights Management
- Talent Cultivation and Development
- Occupational Safety
- Health Care
- Upgrade Your Life
- Social Inclusion
- CSR Milestone
- Economic Aspect
- Environmental Aspect
- Social Aspect
- CSR Report
