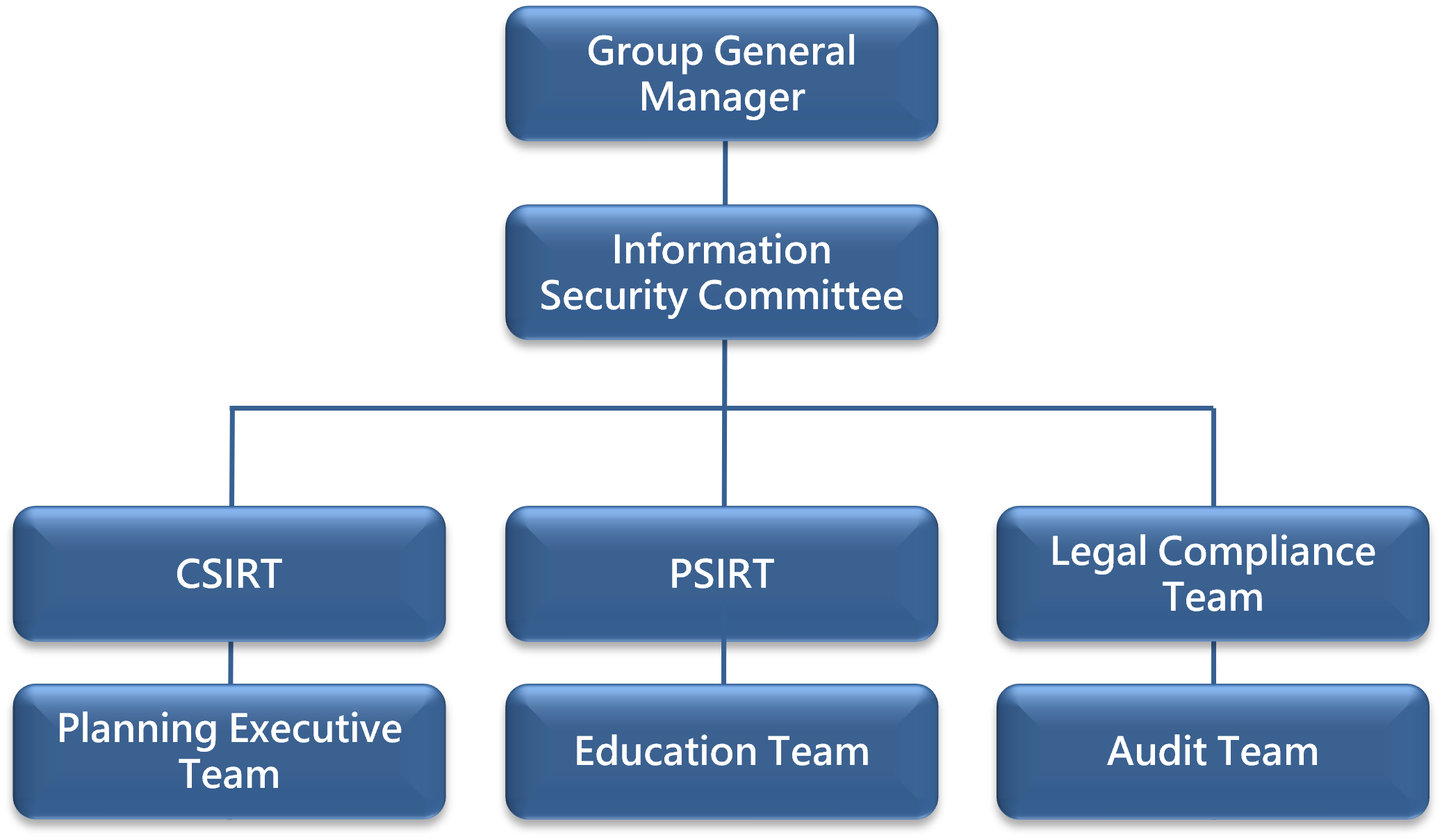
In keeping with the GIGABYTE philosophy of “Upgrade Your Life”, corporate information security governance has been introduced to our continued pursuit of corporate sustainability. The Information Security Committee was set up to devise an information security policy and management framework that takes international standards, regulatory requirements, privacy protection, risk management, and crisis management into account. A total approach to information security management, planning, oversight, and execution has been put into place. The Committee also reports regularly to the President on information security management activities and the overall effectiveness of the management organization.
Governance Organizational Framework
Information Security Policy
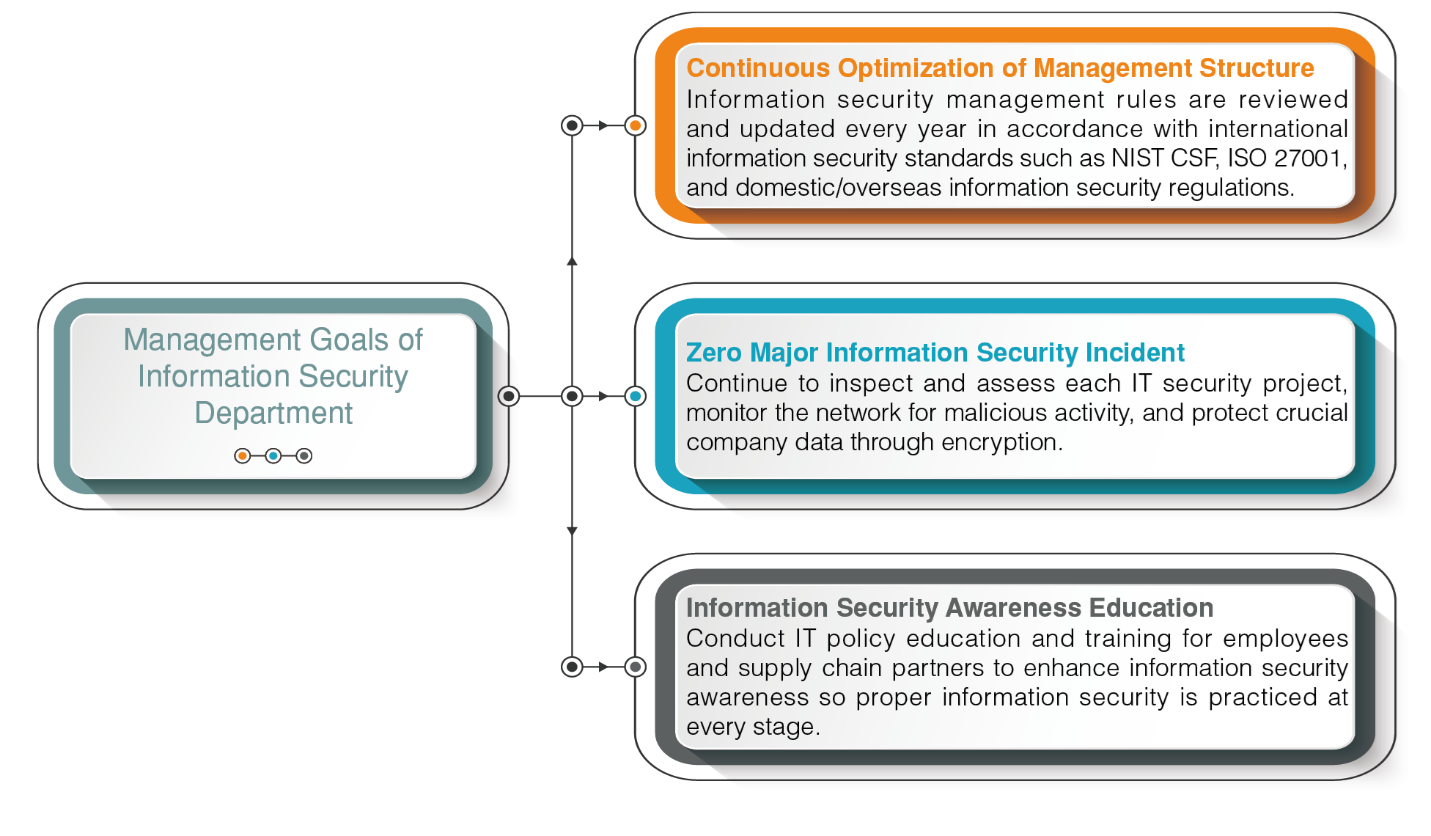
- Information security management rules are reviewed and updated every year in accordance with international information security standards (NIST Cybersecurity Framework) and domestic/overseas information security regulations.
- Ensure the Confidentiality. Integrity) and Availability of information so that they can be applied to the planning, management, and execution of Group business targets in a secure, proper, appropriate, and reliable manner.
- To continue providing customers with a safe and quality product experience, GIGABYTE must ensure that our information security management for R&D processes, product development, cloud services, and manufacturing supply chain all comply with our information security policy. The goal is the effective reduction of management risk and continued improvement to the overall maturity of information security.
- Conduct regular offensive and defensive information security drills, strengthen internal information security awareness through employee training, and implement information security throughout all processes.
Management Goal and Outcome in 2023
Management Framework
- Information security management standards based on the National Institute of Standards and Technology Framework for Improvement Critical Infrastructure Cybersecurity (NIST CSF) were introduced across the board in accordance with our security policy. An information security management framework and Information Security Incident Response Team were set up to support identification, protection, detection, response, and recovery. These five core functions cover the entire information risk management cycle.
- Establishment of high-security protection mechanisms and introduce multi-factor authentication (MFA) to ensure information operations are secure and accurate while employees work from home during the COVID-19 pandemic.
- Establishment of regulations on supplier cybersecurity risk assessment to help suppliers protect their information security, thereby strengthening our collaboration with suppliers on cybersecurity to bolster the competitiveness of the entire supply chain.
- Develop information security risk management specifications for the information supply chain, and integrate them into supplier management.
Information Security Drill
- Conduct vulnerability scanning and penetration testing to systematically and comprehensively verify security defense capability.
- Carry out a drill in information security incident notification and response to fulfill responsibility division and improve handling proficiency.
- Execute third-party vulnerability analyses and hacker attack simulations, and conduct information security incident reporting and response drills at least once a year.
Information Security Training
- Organized 2 education and training sessions on information security policy and security awareness, with 1,255 employees participating.
- To improve security awareness and alertness, intensive classes were held every month for employees who failed social engineering drills. A total of 589 employees participated.
- Held 3 sessions of supply chain information security assessment seminar for suppliers to explain the assessment methodologies and rights and obligations of participation. A total of 154 suppliers participated.
Information Security Incident
- In 2023, no incidents of information security intrusion occurred, and neither customers, consumers, nor employees were affected.
Customer Privacy Protection
GIGABYTE respects the personal information and privacy of our customers. A Personal Information Protection and Management Committee is established in accordance with the governmentʼs “Personal Information and Protection Act” to define and enforce the “Personal Information Protection and Management Regulations”. Proposals for making future improvements to personal information risks are also developed ad hoc to protect customer information. There were no leaks of customersʼ personal information in 2023.
Privacy Protection and Management Regulations
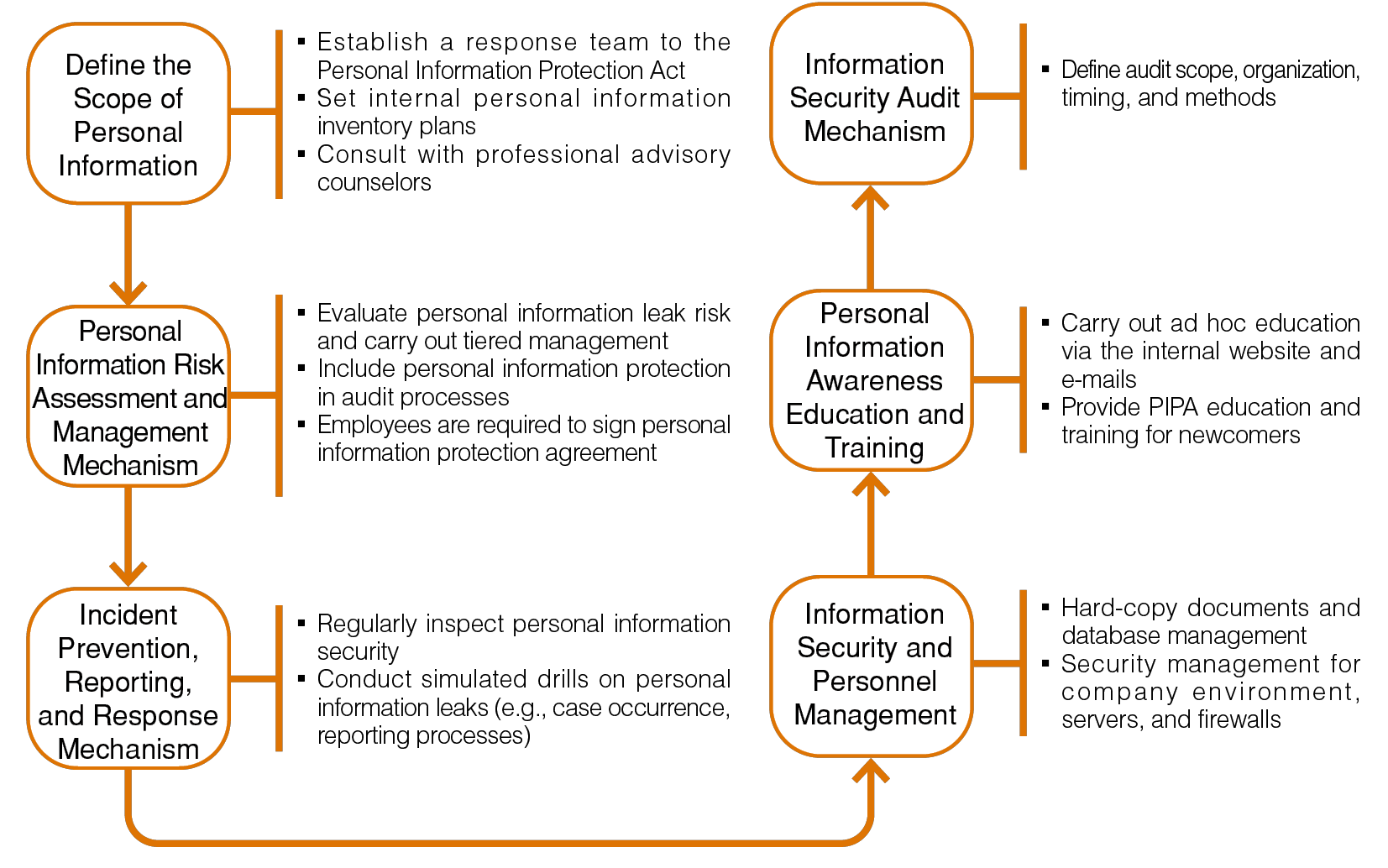
GIGABYTE formulates a privacy policy that governs all Company operations, including suppliers and third-party service providers. All risk management measures are also reviewed to ensure they comply with the Companyʼs security policy and procedures. Compliance reviews include the periodic review and updating of the privacy policy to ensure that its harmonization with the applicable laws and regulations, and complies with the latest compliance requirements. We also continue incorporating industry best practices such as GDPR and CCPA into our privacy policy. For more information, please refer to Privacy Policy.
- Home
- Innovation Management
- The Ocean is Our Home
- From the Chairman
- Commitment to CSR
- Stakeholder Engagement
- Material Topics
- SDGs
- Corporate Organization
- Code of Conduct
- Information Security & Privacy
- Risk Management
- Supply Chain Management
- Tetralogy of Supply Chain Engagement
- Conflict Mineral
- Environmental Management Policy
- Climate Action
- Eco-friendly Product
- Extended Product Responsibility
- Circular Economy
- Green Action
- Sustainability/Environmental Education
- Green Activities
- Working Holiday
- Corporate Volunteering
- Go Green Taiwan
- Make Earth Green Again
- Tree Map
- Overview/Core Concept
- Rooftop Farm
- Ecology Photo Competition
- Sustainability-related Certification
- Human Resource Structure
- Talent Management
- Human Rights Management
- Talent Cultivation and Development
- Occupational Safety
- Health Care
- Upgrade Your Life
- Social Inclusion
- CSR Milestone
- Economic Aspect
- Environmental Aspect
- Social Aspect
- CSR Report
