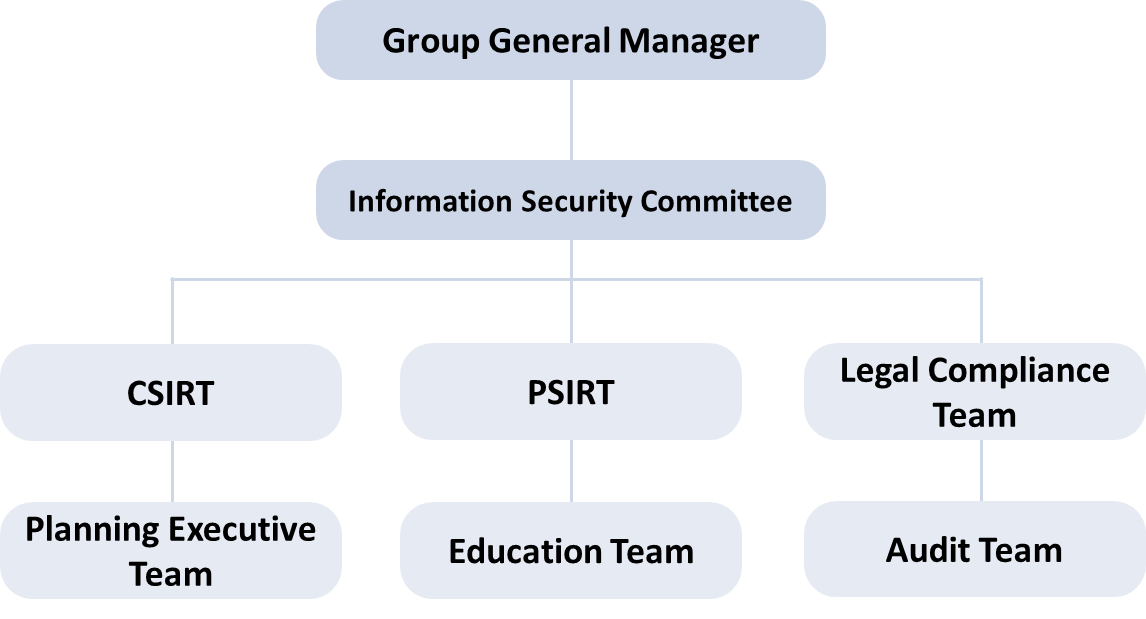
GIGABYTE established an Information Security Committee in 2021. An information security policy and management structure were formulated in accordance with international standards, regulatory requirements, privacy protection, as well as risk and crisis management. Suppliers were also incorporated into scope of management to strengthen joint defense throughout the supply chain. The Committee is responsible for promoting information security management, planning, supervision and implementation across the organization. It also regularly reports to the Group President on the effectiveness of information security management activities and systems by the information security management organization.
The Information Security Management Structure and Security Response Task Force was set up for harmonization with the Cybersecurity Framework (CSF 2.0) developed by the US National Institute of Standards and Technology (NIST). A total information security management standard was introduced to continuously improve information security based on the 5 key indicators of Identify, Protect, Detect, Respond, and Recover. This covers the entire information security risk management life cycle.
To address the expansion of AI server business in 2024, including new products, new suppliers, upgraded customer services, and cybersecurity risks. Group President, Lee, E-Tay who has extensive experience in IT and product information security was designated as the highest convener of the Information Security Committee responsible for directing the Committeeʼs quarterly activities. A Chief Information Security Officer (CISO) and dedicated information security specialists were also appointed. Two social engineering drills and enhanced employee training were carried out to raise employee awareness on adherence to the corporate information security policy and reduce information security management risks.
Governance Organizational Framework
Information Security Policy
- Information security management rules are reviewed and updated every year in accordance with international information security standards (NIST Cybersecurity Framework) and domestic/overseas information security regulations.
- Ensure the Confidentiality. Integrity) and Availability of information so that they can be applied to the planning, management, and execution of Group business targets in a secure, proper, appropriate, and reliable manner.
- To continue providing customers with a safe and quality product experience, GIGABYTE must ensure that our information security management for R&D processes, product development, cloud services, and manufacturing supply chain all comply with our information security policy. The goal is the effective reduction of management risk and continued improvement to the overall maturity of information security.
- Conduct regular offensive and defensive information security drills, strengthen internal information security awareness through employee training, and implement information security throughout all processes.
Information Security Management
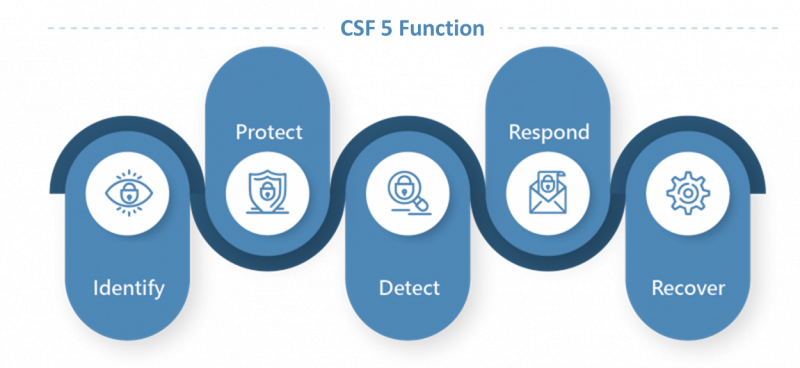
Information Security Risk Management Strategy
| Strategy | Description |
|---|---|
| Information Security Risk Commitment | The Company pledges to build a total information security management system to ensure the confidentiality, integrity and availability of data |
| Privacy Protection Commitment | The Company strives to respect and protect the privacy of customers and employees, and to comply with the relevant privacy regulations (e.g. GDPR) |
| Employee Education and Development | The Company pledges to strengthen the development of the internal information security culture, and to enhance the security awareness and technical ability of employees through periodic training and testing |
| Compliance | The Company pledges to comply with all applicable information security and privacy protection laws and regulations and take active measures to maintain compliance |
| Security Incident Management | The Company pledges to protect the rights and interests of customers and stakeholders by responding swiftly and effectively to security incidents |
Ways of maintaining information security
- Identify the Companyʼs protected information assets and value processes
- Conduct 1 information asset identification and risk assessment every year to establish risk protection measures
- Conduct random information security education and training every year to counter corporate e-mail fraud
- Conduct 2 social engineering drills with enhanced education and training for high-risk employees
- Employ AI technology to conduct real-timing monitoring of incoming traffic to detect suspicious programs and malicious behavior and reduce malicious attacks
- Set up information security response team to establish response mechanisms and conduct simulated attack/defense drills
- Participate in joint defense organizations such as Taiwan Information Security Alliance, Taiwan Chief Information Security Officer Alliance to gain information security experience
- Update response and recovery plans when there is a change in business structure to prevent business disruptions due to information system errors
Information Security Incident in the past 3 years
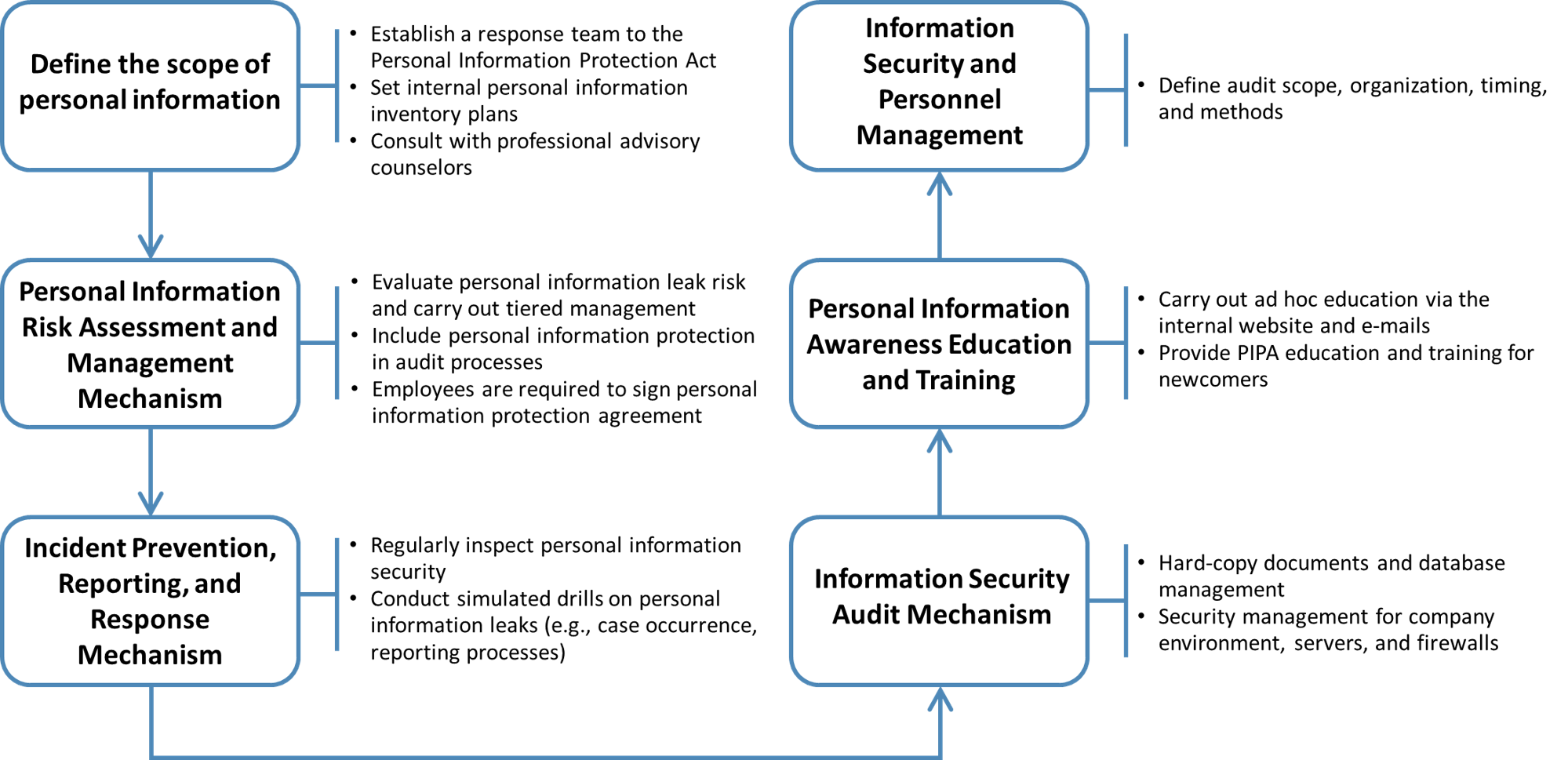
Information Security Risk Management and Response Mechanism
▋ Information security management and audit
To improve our response to information security risk management, we review our information security risk exposure at least twice a year to identify our information security risk appetite. This includes stress testing and sensitivity analysis to establish the relative priorities of information security risks. Actions are then taken to mitigate information security risks. All of the above information security risk management processes undergo internal/external audits. The validity of ISO/IEC 27001:2022、CNS 27001:2023 information security management system certifications are also maintained for information devices and the information security management system.
ICT security has been included in the internal audit plan for 2025, with the audit scheduled to take place in Q4.
▋ Promotion of technological upgrades and information security defenses
Data encryption technology, multi-factor authentication, intrusion detection system, and AI security analysis tools were introduced to improve our ability to defend against online threats and reduce the risk of data leakage. At the same time, protection against internal information security attacks was also strengthen using firewall hardware, deployment of intrusion detection systems, periodic vulnerability scanning and penetration testing of external websites, and conducting at least 1 response drill procedure each year. As a result, the Company maintained an A rating (highest level) for information security and maturity in 2024.
▋ Information security education and training
We have designed and are progressively implementing our information security management policy. Internal information security rules have been published with an explicitly defined information security complaints process to ensure that employees can follow the SOP to make a report when they notice any suspicious activity. At the same time, we have incorporated IT and cybersecurity into employees’ performance evaluations. Information security and privacy protection training courses are regularly held as well to improve the information security awareness and response ability of all employees. For supplier management, we are applying the Information Security Risk Management Regulations for the Information Supply Chain by requiring suppliers to comply with the relevant policies. We also introduced and incorporated information security audits into supplier management to help suppliers improve their information security capabilities. By actively enhancing the information security awareness and ability of both internal and external stakeholders, we can ensure the full compliance of the Company and reduce the risk of heavy financial penalties or legal repercussions due to the leakage or improper handling of data. In 2024, we conducted education and training on 3 topics that were attended by 2,464 people and amounted to 2,122 training hours. The information security policy and awareness training course was completed by 100% of employees at our Xindian headquarters.
2024 Information security education and training performance
| Course Name | Target | Participation | Duration (hours) |
|---|---|---|---|
| Information Security Policy and Awareness Training | Employees at Xindian Headquarters | 1,288 | 1,288 |
| Remedial Social Engineering Class | Employees that failed the drill | 1,012 | 506 |
| Supply Chain Information Security Evaluation Seminar | Suppliers | 164 | 328 |
| Total | 2,464 | 2,122 | |
Note: The scope of the ISO/IEC 27001:2022 and CNS 27001:2023 information security management system certifications only encompasses the Xindian headquarters. Therefore, the participants in the education and training were primarily employees from the headquarters.
Customer Privacy Protection
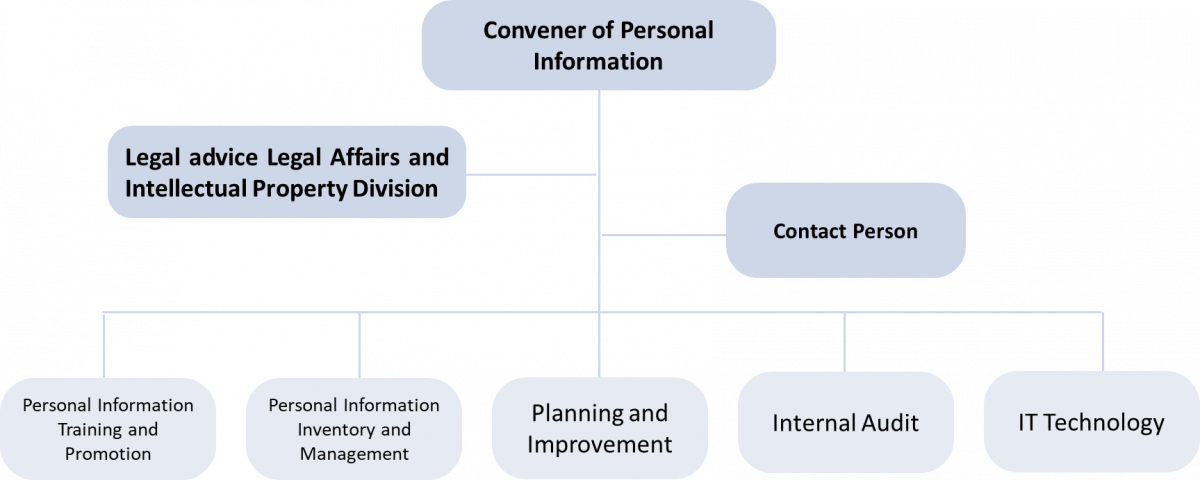
GIGABYTE respects the personal information and privacy of our customers. A Personal Information Protection and Management Committee is established in accordance with the governmentʼs “Personal Information and Protection Act” to define and enforce the “Personal Information Protection and Management Regulations”. Proposals for making future improvements to personal information risks are also developed ad hoc to protect customer information.
“GIGABYTE Personal Data Management Policy” has been established in 2014. At the same time, In the event of any incident raising concerns about violations of personal data privacy and protection, the relevant departments will initiate an investigation. If the investigation confirms a breach of this policy or applicable laws, disciplinary actions will be taken against the personnel involved in accordance with relevant regulations, and legal liability will be pursued when necessary.
There were no leaks of customersʼ personal information in 2024.
GIGABYTE formulates a privacy policy that governs all Company operations, including suppliers and third-party service providers. All risk management measures are also reviewed to ensure they comply with the Companyʼs security policy and procedures. Compliance reviews include the periodic review and updating of the privacy policy to ensure that its harmonization with the applicable laws and regulations, and complies with the latest compliance requirements. We also continue incorporating industry best practices such as GDPR and CCPA into our privacy policy. For more information, please refer to Privacy Policy.
Privacy Protection and Management Regulation
Personal Information Protection and Management Committee
- Home
- Innovation Management
- The Guanxi Blue Zone
- The Ocean is Our Home
- From the Chairman
- Commitment to CSR
- Stakeholder Engagement
- Material Topics
- SDGs
- Corporate Organization
- Code of Conduct
- Information Security & Privacy
- Risk Management
- Supply Chain Management
- Tetralogy of Supply Chain Engagement
- Conflict Mineral
- Environmental Management Policy
- Brand Strategy and Business Reputation Management
- Climate Strategy and Risk Management
- Customer Relations Management
- Eco-friendly Product
- Extended Product Responsibility
- Biodiversity
- Circular Economy
- Green Action
- Sustainability/Environmental Education
- Green Activities
- Working Holiday
- Corporate Volunteering
- Go Green Taiwan
- Make Earth Green Again
- Tree Map
- Overview/Core Concept
- Rooftop Farm
- Ecology Photo Competition
- Resource Hub
- Diverse and Inclusive Workplace
- Talent Management
- Human Rights Management
- Talent Cultivation and Development
- Occupational Safety
- Health Care
- Upgrade Your Life
- Social Inclusion
- CSR Milestone
- Economic Aspect
- Environmental Aspect
- Social Aspect
- CSR Report
